An exclusive article by Fred Kahn
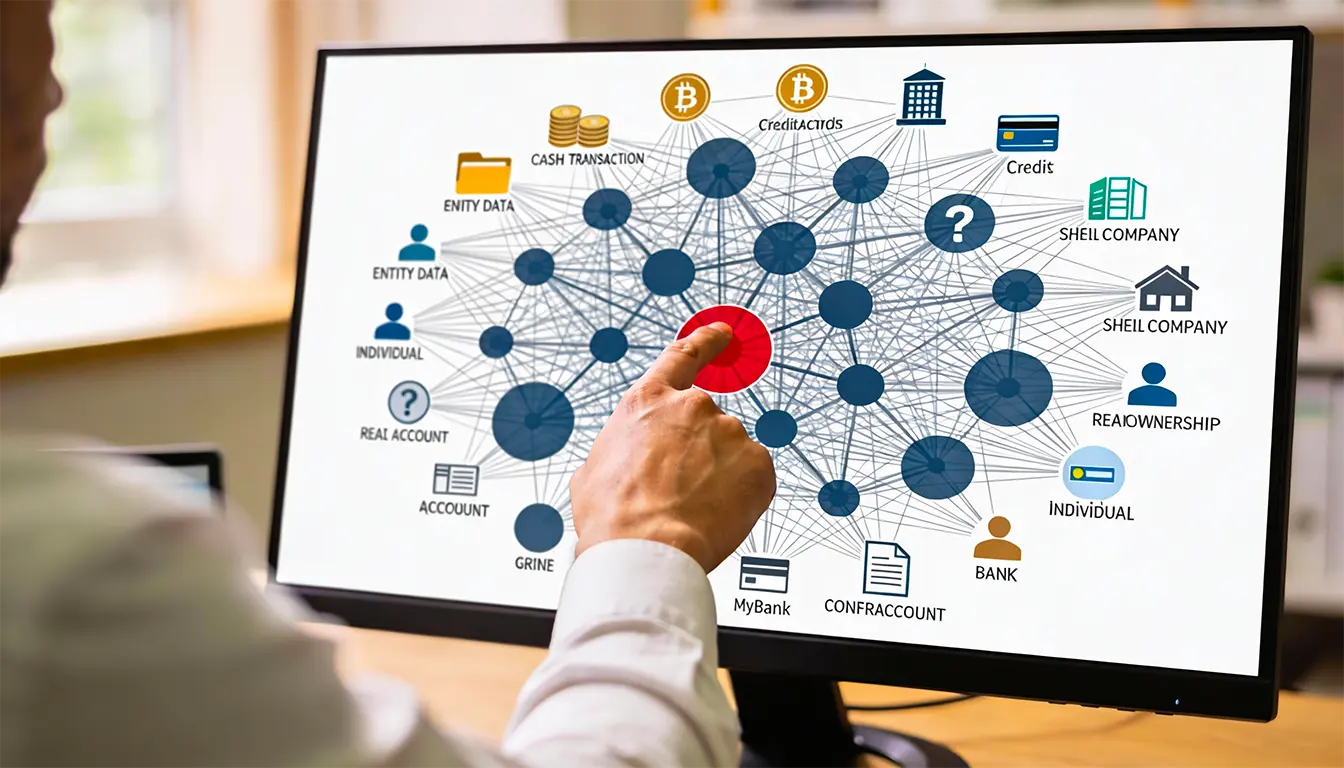
Financial institutions globally struggle with a significant rise in the complexity of illicit networks that exploit fragmented data architectures. The integration of high-fidelity data from multiple origins, including know your customer profiles, granular transaction histories, real estate ownership records, and blockchain transaction ledgers, allows for a comprehensive view of risk that isolated systems cannot achieve. By merging these disparate datasets into a single analytical framework, investigators can immediately recognize when a low-income account holder suddenly acquires high-value property or when multiple shell companies share the same physical address across different registries. This holistic data graph strategy transforms raw information into actionable intelligence, facilitating the detection of sophisticated layering techniques that rely on the separation of identity and activity. Transitioning to a unified datagraph ensures that these multi-dimensional relationships are visible, enabling the discovery of non-obvious connections and overlapping beneficial ownership that are essential for effective risk mitigation.
Table of Contents
Enhancing Investigative Precision Through Graph Analytics
The primary benefit of a unified datagraph lies in its ability to break down the silos that typically separate customer identity data from real-world financial activity. In a standard relational database, investigators must perform manual joins between tables to see how a specific entity relates to a series of transactions. This process is often slow and prone to error, especially when dealing with thousands of data points. By using graph technology, every account, individual, and transaction is treated as a node connected by edges, representing relationships like ownership or fund transfers. This structure allows for the immediate visualization of high-risk clusters, such as several independent accounts sharing a single physical address or a common beneficial owner. These patterns are frequently the hallmarks of shell company networks or smurfing operations, where small sums are moved across many accounts to avoid detection thresholds.
Detecting these hidden links is crucial because money launderers rarely operate through a single direct path. They instead use circular payments and multi-hop transfers to obscure the source of funds. A datagraph enables investigators to run pathfinding algorithms that can trace the flow of capital through ten or more layers of separation in milliseconds. Traditional systems would struggle with the computational load required to perform such deep-link analysis, often timing out or returning incomplete results. Furthermore, the integration of entity resolution within the graph ensures that variations in name spellings or address formats do not prevent the system from recognizing that two seemingly distinct profiles actually belong to the same person. This synthesis of fragmented data creates a single source of truth, allowing analysts to spend less time on manual data stitching and more time on high-value strategic discovery.
Technical Architecture for Unified Financial Intelligence
Building a single datagraph requires a shift from traditional SQL databases to specialized graph database management systems. These systems are designed to store relationship data as a first-class citizen, meaning the links between nodes are stored physically on the disk rather than being calculated at the time of a query. From a technology perspective, this requires high-performance hardware capable of handling massive in-memory computations, as graph traversals are resource-intensive. Financial institutions must also implement robust ETL pipelines to ingest data from heterogeneous sources, including core banking systems, KYC registries, and external sanctions lists. These pipelines must be capable of real-time or near-real-time updates to ensure that the graph reflects the most current state of the financial network.
Beyond the database layer, the implementation of graph neural networks represents the next frontier in automated detection. These models can learn the typical topology of a legitimate user’s network and flag deviations that suggest illicit behavior. For instance, a graph-based machine learning model might identify a sudden influx of connections from a high-risk jurisdiction as a precursor to a laundering event, even if the individual transactions do not trigger traditional rule-based alerts. The technology stack must also include intuitive visualization tools that allow human investigators to interact with the graph. A single pane of glass approach, where an analyst can click on a suspicious node to see every related entity and transaction history, dramatically accelerates the triage process and improves the quality of suspicious activity reports. This technological leap allows for the discovery of hidden dependencies that a flat file system simply cannot process without significant manual intervention and time.
Overcoming the Limitations of Legacy Monitoring Systems
Traditional monitoring systems often rely on threshold-based alerts that monitor individual accounts in isolation. This siloed approach is easily exploited by sophisticated criminal syndicates who distribute their activities across multiple jurisdictions and institutional entities to keep individual transaction volumes below reporting triggers. By moving to a datagraph model, investigators can apply community detection algorithms that identify groups of accounts acting in a coordinated manner, regardless of individual account limits. These algorithms analyze the density and frequency of connections to flag networks that exhibit abnormal structural properties, such as high-velocity churning of funds through a central hub node.
The implementation of such a system also enhances the ability to perform look-back investigations with greater depth. When a new entity is added to a sanctions list, a graph-enabled system can instantly query the entire network to find not just direct hits, but second and third-degree connections that may be acting as proxies. This level of automated link analysis is virtually impossible in legacy systems without days of manual data extraction and correlation. By automating the discovery of these indirect associations, financial institutions can significantly reduce their exposure to regulatory risk and ensure that their compliance programs are robust enough to withstand the scrutiny of modern auditors. The shift from a transaction-centric view to a relationship-centric view is the fundamental change required to address the sophistication of modern financial crime.
Advancing Toward Proactive Risk Mitigation
The ultimate goal of adopting an integrated datagraph is to move from a reactive stance to a proactive one. Currently, many compliance teams are overwhelmed by a tsunami of false positives generated by brittle, rule-based systems. By providing a contextual view of risk, graph technology helps filter out noise and prioritize the most serious threats. If an alert is triggered on a single transaction, the graph can instantly show if that transaction is part of a larger, coordinated effort involving multiple accounts and known bad actors. This level of insight is essential for meeting the evolving standards set by international bodies like the Financial Action Task Force, which increasingly emphasizes the need for a risk-based approach supported by advanced data analytics.
As we look toward the future of financial crime prevention, the ability to map the entire ecosystem of an entity will become a standard requirement. The integration of unstructured data, such as the narrative sections of previous reports or news articles, into the graph will further enrich the investigative context. This allows for the discovery of unknown unknowns, the subtle relationships and emerging typologies that define modern financial crime. Organizations that invest in these technologies not only protect themselves from potential regulatory failures but also contribute to the overall integrity of the global financial system by making it significantly harder for illicit actors to hide their activities in plain sight. Through the persistent application of these data structures, institutions can finally close the gaps that have allowed illicit capital to flow through the shadows of the global economy for decades.
Key Points
- Integrated datagraphs combine entity and transaction data to reveal hidden connections like shared addresses or beneficial owners.
- Graph databases outperform traditional SQL systems by allowing deep-link analysis across multiple layers of transactions in real-time.
- Entity resolution within the graph prevents criminals from using slight data variations to hide their true identity across systems.
- Advanced graph machine learning models can detect suspicious network topologies that standard rule-based alerts frequently miss.
Related Links
- FATF Guidance on Digital Identity and Data Analytics
- European Banking Authority Report on AML Compliance in Crypto-Assets
- United Nations Office on Drugs and Crime Money Laundering Overview
- FinCEN Guidance on Beneficial Ownership Reporting Requirements
Other FinCrime Central Articles About the Benefits of Data Graphs
- Revealing Hidden Connections: How Universal Data Linkage Can Revolutionize Financial Crime Detection
- Uncovering Risk Faster and Better Using Combined Data Sources for Financial Crime Investigations
- Revealing Hidden Connections: How Universal Data Linkage Can Revolutionize Financial Crime Detection
Some of FinCrime Central’s articles may have been enriched or edited with the help of AI tools. It may contain unintentional errors.
Want to promote your brand, or need some help selecting the right solution or the right advisory firm? Email us at info@fincrimecentral.com; we probably have the right contact for you.